13 Jun 2014 You Can’t Protect What You Don’t See
Why visibility into all data channels is critical for data protection
Data Loss Hits Your Bottom Line
 In this age of sophisticated advanced persistent threats (APTs) and targeted, zero-day exploits, protect- ing sensitive corporate data is more challenging than ever. Daily reports of damaging exploits against large well-known organisations such as Sony, Target, Google and others have become the norm rather than the exception. These losses can compound quickly and may include the financial burden of lawsuits and huge regulatory fines for compliance violations; brand damage leading to customer attrition and loss of revenue; intellectual property loss resulting in competitive disadvantage and more. At the high end of the financial spectrum, the Sony PlayStation breach was reported to have cost Sony a total of one billion dollars, in the final analysis. At the other end of the spectrum, the cost to organisations is just as significant. The Ponomen Data Breach Study, which focused solely on incidents involving 100,000 records or less, found an average data breach cost of $5M per incident, a financial blow that many organisations would find difficult to absorb.
In this age of sophisticated advanced persistent threats (APTs) and targeted, zero-day exploits, protect- ing sensitive corporate data is more challenging than ever. Daily reports of damaging exploits against large well-known organisations such as Sony, Target, Google and others have become the norm rather than the exception. These losses can compound quickly and may include the financial burden of lawsuits and huge regulatory fines for compliance violations; brand damage leading to customer attrition and loss of revenue; intellectual property loss resulting in competitive disadvantage and more. At the high end of the financial spectrum, the Sony PlayStation breach was reported to have cost Sony a total of one billion dollars, in the final analysis. At the other end of the spectrum, the cost to organisations is just as significant. The Ponomen Data Breach Study, which focused solely on incidents involving 100,000 records or less, found an average data breach cost of $5M per incident, a financial blow that many organisations would find difficult to absorb.
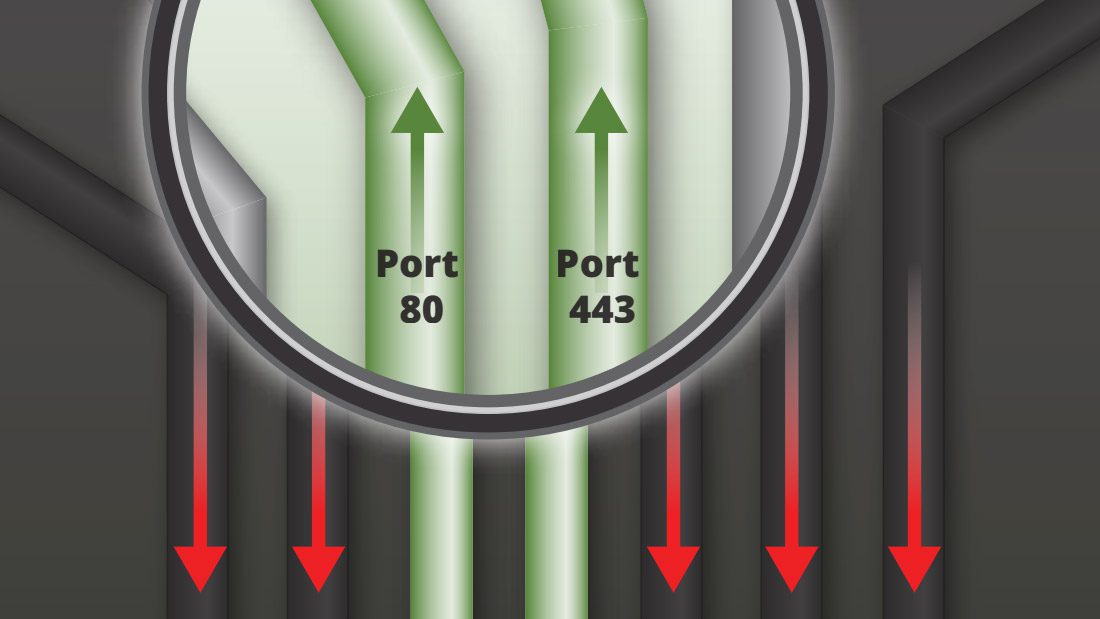
Unfortunately, many current network security solutions may not be providing adequate protection against these losses because they are ignoring data channels that are ripe for exploitation, including a vast number of UDP ports. If your security solution doesn’t give you visibility into all 131,070 of the data channels, or ports, that may be accessing your network, you are at risk. Port-evasive attacks that take advantage of the unseen ports on corporate networks are becoming more common. For example, recent data breaches against Visa and JC Penney involved SQL injections implemented using port-evasive techniques. The questions of how an attacker might try to get data out of your network and whether your current security solutions offer the visibility you need to protect all your data channels, are ones to consider as you strive to implement a comprehensive security strategy for your organisation. This white paper discusses port vulnerabilities you may not have considered and explains how visibility into unseen ports can increase your network security profile.
The Cost of Corporate Data Loss
Results from the 2013 Ponomen Research on Data Breaches shows:
- Organisations in the US had
29,000 incidents of data breaches involving 100,000 records or less - Average cost of incidents involving criminal or malicious malware was $277 per record ($27M total)
- Globally, the US had the highest cost per data breach – $5M per incident
Channels for Data Transfer have Evolved
In the early years of the Internet, most data was transmitted through ports 80 and 443, the standard ports used for HTTP and later, HTTPS traffic, respectively. These TCP channels are used to fetch Web pages, PDFs, JavaScript and similar data. The early Internet was not as dynamic as it has become, with very few applications even requiring an Internet connection. The widely used business software of the time – programs such as Word and Excel didn’t require the Internet and businesses were able to operate efficiently on what was basically a two-lane highway, using port 80 for most Web traffic and port 443 for encrypted traffic.
The Rise of Web 2.0
With the evolution of the Internet leading to Web 2.0 and the explosion of applications requiring an Internet connection, more ports are now being used to transfer an ever-widening range of data. Today’s TCP traffic uses 65,535 ports and UDP employs another 65,535 ports providing over 131 thousand ports, each with a unique number that enables data to be delivered and received at the same time. The availability of so many channels supporting multiple streams of inbound and outbound traffic has contributed to the speed and efficiency of the Web, but this complexity also lends itself more easily to exploitation by cybercriminals. They are becoming increasingly adept at capitalising on network vulnerabilities, including the availability of multiple ports and protocols.
Two Types of Data Channels or Ports:
| Transmission Control Protocol – TCPTCP is a connection-oriented protocol primarily used to deliver files such as PDFs, emails, and Web pages. TCP operates by transferring data in pieces or packets and then reassembling them at their destination. Built into the TCP connection are extra handshakes and other measures that assure the data is delivered without error.When a PDF is downloaded, for instance, the Internet breaks it into packets, which are reassembled at the endpoint so the file can be viewed. If one of the packets is missing, it is automatically resent by the TCP protocol so the down- load arrives intact.Without the TCP protocol, the user would receive an error that the PDF was corrupt due to the missing packet. |
VS |
User Datagram Protocol – UDPIn contrast to TCP, UDP is a faster and less complex protocol. It was designed to deliver data in datagrams, or independent packets of binary data transmitted over the network. While TCP uses techniques that assure packets are delivered in a specific order so they can be reassembled, UDP delivers its individual packets in no particular order, but at a much greater speed. This makes UDP the ideal protocol for sending streaming video from popular services such as Netflix, Hulu, Pandora, Amazon and many others. If one packet or piece of the video file is missing, the viewer may see a blip on the screen, but it represents a minimal interruption in the viewing experience.In another example, UDP is also used for VoIP (voice over IP) communications, where retransmitting parts of a conversation would likely create an echo, making the conversation unintelligible. |
Popular Applications That Use UDP Ports Include:
| Communication & Collaboration | Streaming | File Sharing | Anonymous Browsing | ||||
 |
 |
 |
 |
 |
 |
 |
 |
| Netflix | YouTube | iCloud Drive | Dropbox | Ultrasurf | Tor | ||
 |
 |
 |
 |
 |
 |
 |
 |
| Skype | Spotify | Vimeo | Google Drive | Bitorrent | Tunnel Bear | Cyber Ghost | |
How TCP and UDP Work with Traditional Network Security
Organisations have long understood that managing their data channels is an integral part of comprehensive network security, but many vendors have failed to keep pace with the Web 2.0 environment. This is partly due to the challenges of securing UDP vs. TCP traffic.
| TCP – Easier to Secure | UDP – Difficult to Secure |
| TCP plays well with network security primarily because it’s much easier to quickly terminate a connection if a malicious transfer is detected. All that’s required is to inject a TCP reset packet, which is built into the protocol and works by indicating to both sides of the communication channel that the connection should be immediately terminated. Although this packet is injected by the security solution, the receiving sides do not know that it was spoofed and quickly terminate the transfer. | UDP traffic does not cooperate as well with network security, primarily because there is no way to inject a UDP reset packet that could terminate a transfer. In fact, reset packets for UDP don’t exist – each packet is independent of the others and the opportunity to reset is not built into the protocol. This makes it very difficult to interrupt the delivery of the fast, continuous data streams that typically use this protocol. |
Closing UDP Channels is Not the Answer
One might think that simply closing all channels except ports 80 and 443 would be an easy way to assure security. This is not a viable solution for organisations today, nor is blocking all UDP traffic. One reason is that important services such as DNS (Domain Name System) rely on UDP to deliver domain addresses, and blocking those ports could jeopardise business-critical processes. In addition, many of the applications that organisations rely on every day for efficient communication and collaboration use UDP ports including IM, Outlook, GoToMeeting, Ado- be Creative Cloud, VoIP and many more.
Cybercriminals are Exploiting Open and Unseen Ports
Just as developers have struggled to evolve network security to meet the challenges of the Web 2.0 environment, cyber criminals have been quick to exploit its inherent vulnerabilities. Software that scans for open ports across an IP address are readily available so that open ports are easily detected. In addition cybercriminals are leveraging the complexity of the Web 2.0 environment to employ multiple ports and protocols to launch exploits.
Once a hacker finds an open port, he can fake a connection to get in. He can then probe the port to find vulnerabilities such as misconfigurations, buffer overflows or outdated software giving the intruder a range of options for circumventing your network security and compromising your data, including SQL injections, botnets or other malicious exploits. A botnet exploit involves gaining ac- cess to deposit a bot, which is an independent executable piece of malware. A bot can stay hidden in your network for weeks or even months until it finds an opportunity to communicate with command and control outside. The infected computer then comes under the control of the hacker, as part of a bot network or botnet that can be programmed for a variety of actions, including transferring your data out. These exploits use multiple ports and protocols and can be difficult to detect. For instance, hackers can deliver sensitive data out of the network using a botnet by piggybacking the data on DNS queries. Since DNS transfers commonly occur hundreds of times a day on the network, they are often ignored by traditional network security solutions.
Today, many of the attacks aimed at stealing data are being launched and controlled from non-US locations, with several countries showing up as hot spots for cybercriminal activity. This might make it easier to identify suspicious data transfers, but if you don’t have continuous visibility into where your data transfers are going and how much data is being sent, it could be weeks or even months before you discover a problem, as has been the case in many of the high profile cases that are front page news.
The sophistication and proliferation of today’s advanced threats is why many security experts contend that it’s not a question of whether or not your network will incur an infection, it’s a question of when.
Traditional Web Security Solutions are not Keeping Up
Many traditional Web security solutions have been slow to meet the demands generated by the Web 2.0 environment and the increase in advanced threats, many involving port-evasive techniques. These solutions often lack the tools required to fight today’s quickly-evolving threats:
- Many solutions provide simple content scanning of ports 80 and 443, which is only the tip of the iceberg when it comes to protecting your data. APTs, zero-day attacks and other complex threats use multiple techniques that easily evade the defences of traditional Web security solutions.
- Torrent and other file-sharing applications use multiple ports and protocols to circumvent network security. Solutions that aren’t able to monitor and analyse all port traffic are open to circumvention techniques and subsequent data loss.
- Some solutions are not deployed in-line. When your security solution is out-of-band, you are unable to stop UDP transfers leaving the network, opening many conduits for data theft.
- Traditional security solutions rely on signature based threat detection that scans for known threats, offering no real-time protection against zero-day and other advanced threats.
- Many solutions are unable to give you critical real-time behavioural information such as where your data is going and the amount of data being transferred and when it’s leaving, nor can they show you how this compares to your typical network traffic patterns.
- Most solutions lack the capability to stop UDP data transfers in midstream even if a problem is suspected. Your data is gone before you have any time for mitigation.
Key Criteria for Selecting a Network Security Solution
If shutting down the UDP data channels on your network is not an option and your current security solution isn’t giving you the port visibility you need, how are you going to prevent intrusions and the risk of costly data breaches? Here are some attributes you should look for in a comprehensive security solution that can deliver protection across all ports:
Granular, packet-level visibility – An effective solution needs to be able to inspect all data as it moves in and out of your network. A solution that provides granular packet-level visibility into network traffic across all 131,070 ports, including TCP and UDP traffic, is critical in defending against costly data loss. Without this level of port visibility, even the most sophisticated threat detection measures can fail.
Multi-layered approach – Look for a solution that provides multiple layers of protection across all data channels including application controls and deep-packet inspection in addition to employing standard signature and heuristic-based techniques.
Behavioural anomaly detection
– Establishing a baseline for your network traffic and then analysing the flow of data transfers against that baseline to detect anomalies can add a critical layer of security to your data protection strategy. This capability should include continuous scanning that shows how much data is being transferred, where it is going and how often it is leaving your network.
Real-time alerts and data stream locks – Stopping zero-day threats leading to data loss requires the ability to stop UDP data transfers mid-stream, with enough advanced warning to give IT administrators the time to mitigate the problem and prevent any damage.
Key Questions When Evaluating a Network Security Solution:
- Can it scan traffic across all 131,070 ports?
- Does it scan both the TCP and UDP protocols?
- Can it understand and scan protocols beyond HTTP?
- Is it able to run in-line with your network traffic in order to be effective on UDP streams?
- Does it have the functionality to continuously scan your network traffic to detect behavioural data anomalies?